Favorite Tips About How To Detect Conficker On Your Network

In the nessus scan policy.
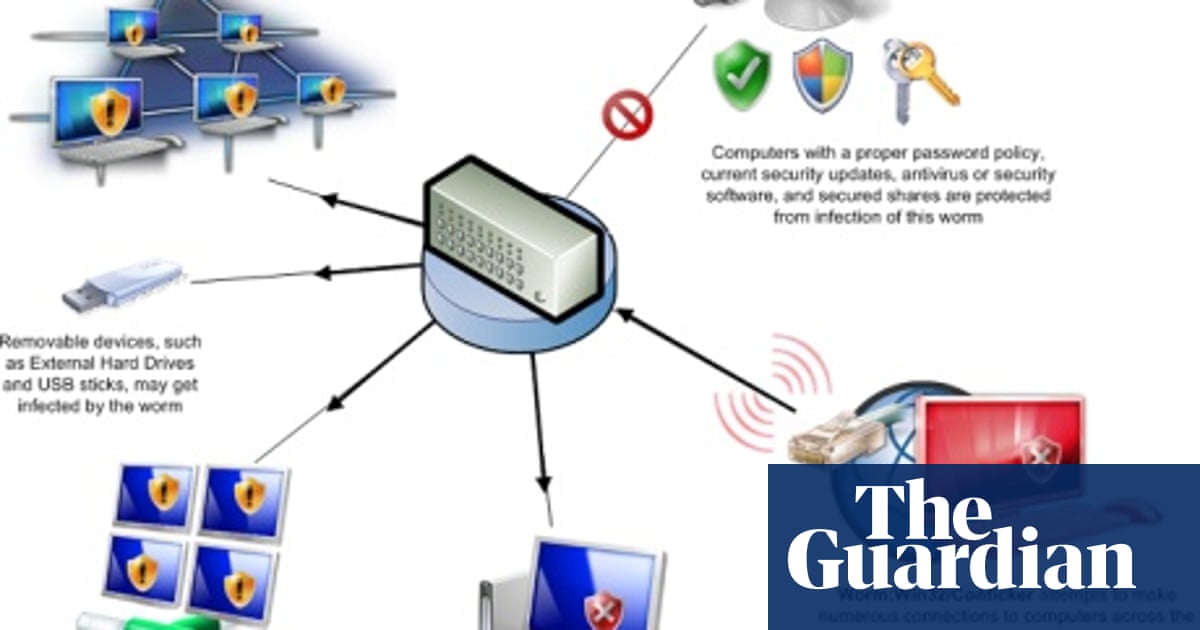
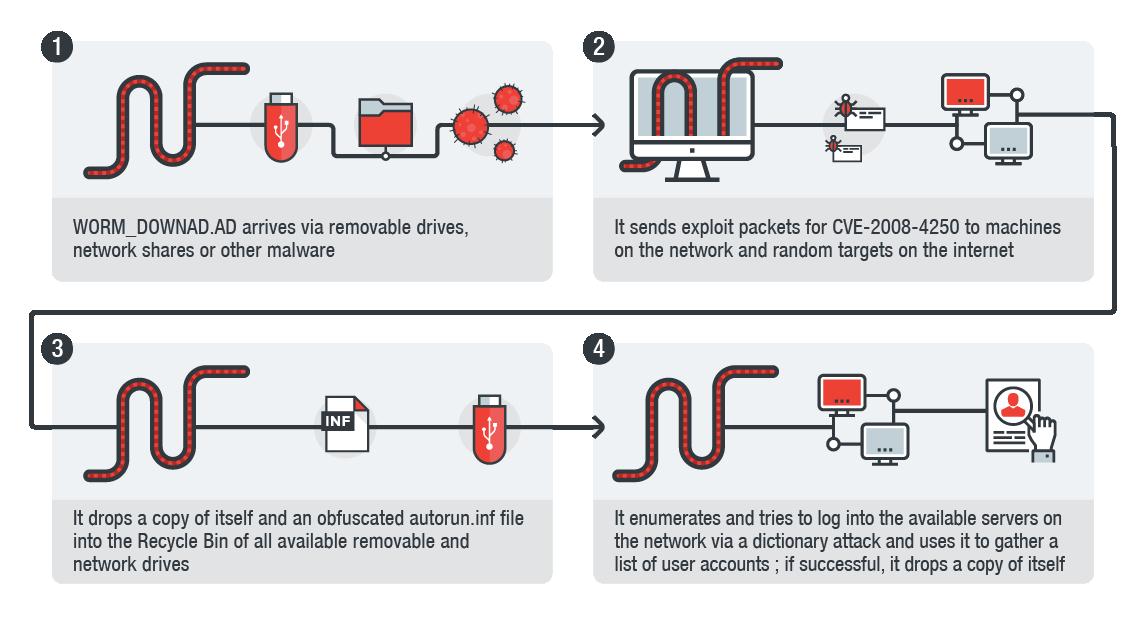
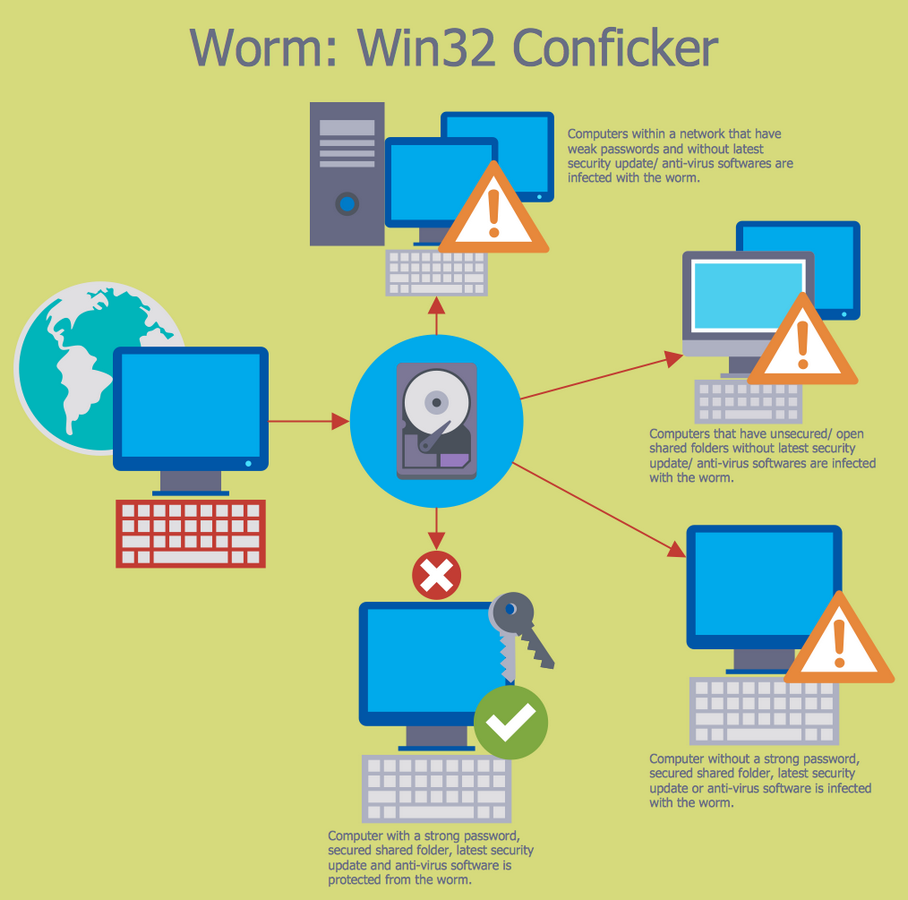
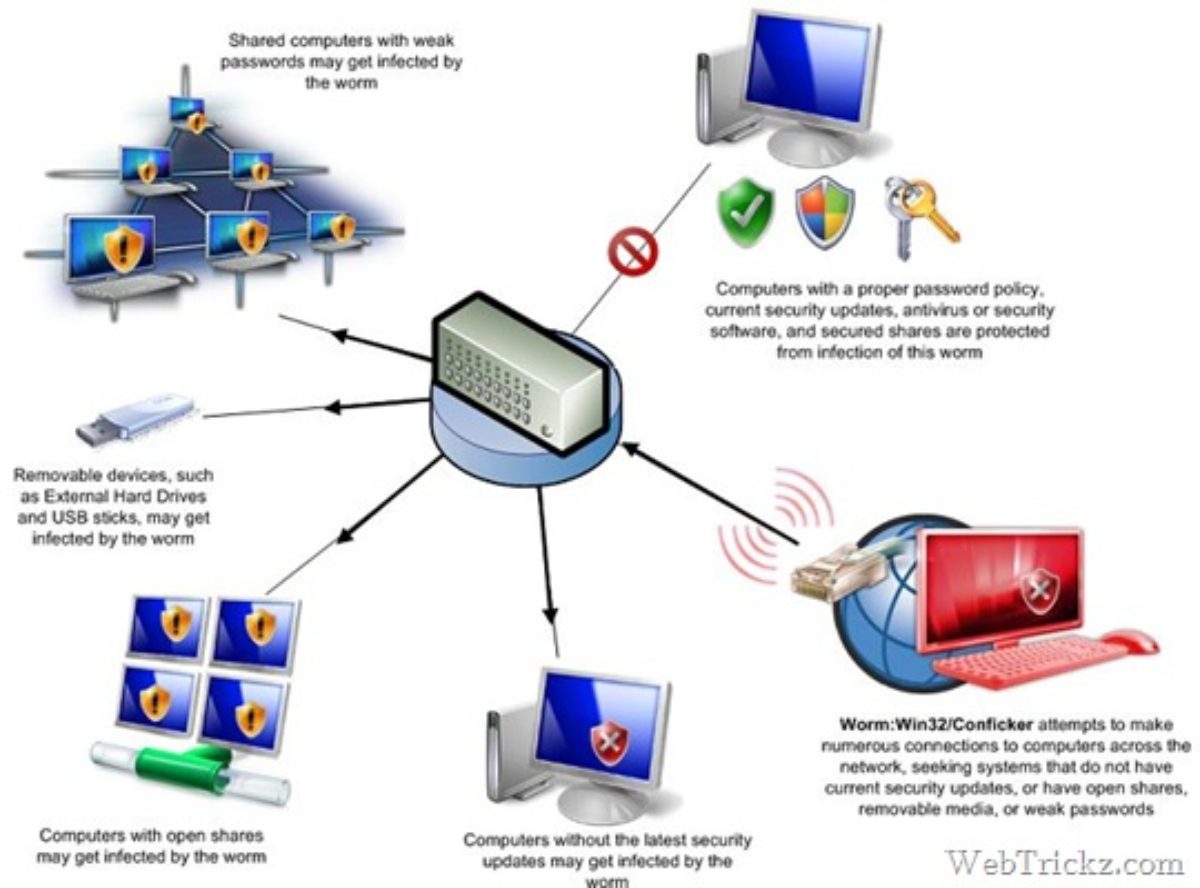
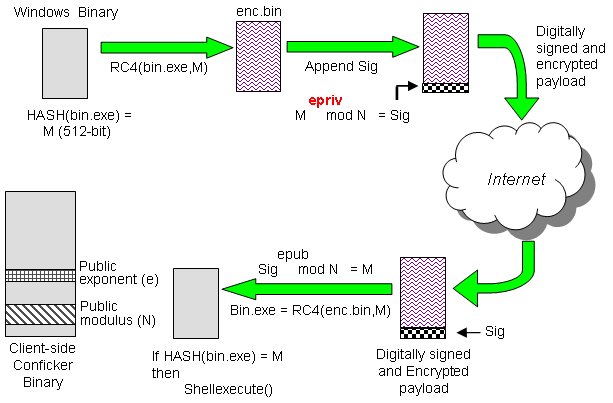
How to detect conficker on your network. Conficker[1] is a computer worm spreading on windows operating system by mainly using a buffer overflow[2]. In the search box, type “network & sharing center.”. After being infected i tried using the enigma conficker remover tool, which first cleaned my system, the problem is that after i got connected to a computer on the network or.
The conficker/downadup worm, which first surfaced in 2008, has infected thousands of business networks. You will need to track down the unprotected computers that are. Open the new gpo, and then move to the following folder:
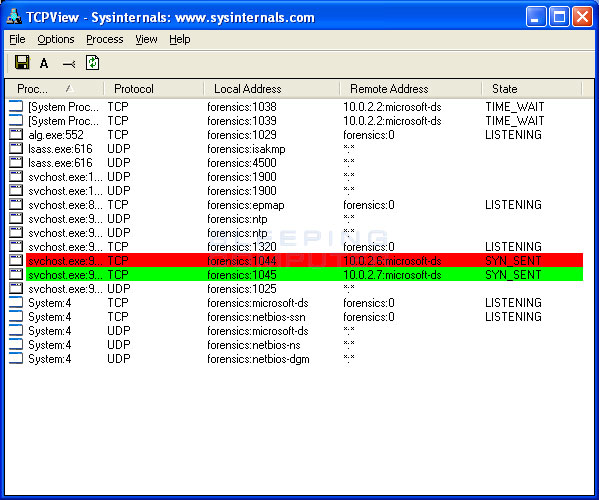
The latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm makes to the port 139 and port 445. This report details the time (utc or gmt unless stated otherwise), protocol, source address and port, and destination address and port of connections related to conficker infections. “msrpc” application identifies microsoft rpc messages which are used to spread conficker.
When there's a large number of traces of malware or worms, for example conficker, that have infected a computer, the only remedy may. Generally, if you are using windows 7 or later edition, you are safe from. If you suspect that a conficker infection is in place on computers in your network, you can use the free utility nmap to detect infected clients using the following commands:
I was able to use the nmap utility. Unpatched computers are most at risk of infection, with conficker exploiting these. Select the tab labeled “internet protocol version 4.
One of the quickest and easiest ways to tell if you are infected with conficker virus is to look below and see if any of the images from four of the 100+ security sites blocked by. Up to 24% cash back how to determine whether your system is vulnerable to conficker or not? I figure everyone is good and ready for tomorrow but just in case you want to double check or still need to scan your network here is a quick and easy method with nmap.





/cloudfront-us-east-1.images.arcpublishing.com/gray/H625APTEBJCF7C5NR4PHG25M7A.jpg)